Discover How Our Cutting-Edge Technology Keeps You Secure
CYTRIX scanner is helping all businesses, both SMBs and enterprises, to test their online assets and products for over 9000 vulnerabilities.
CYTRIX’s mission is to make penetration testing accessible for all. Individuals, small and large companies alike.
Backed by professional cyber security experts holding the same vision and offering their services through CYTRIX.
Let’s make the world safer, together.
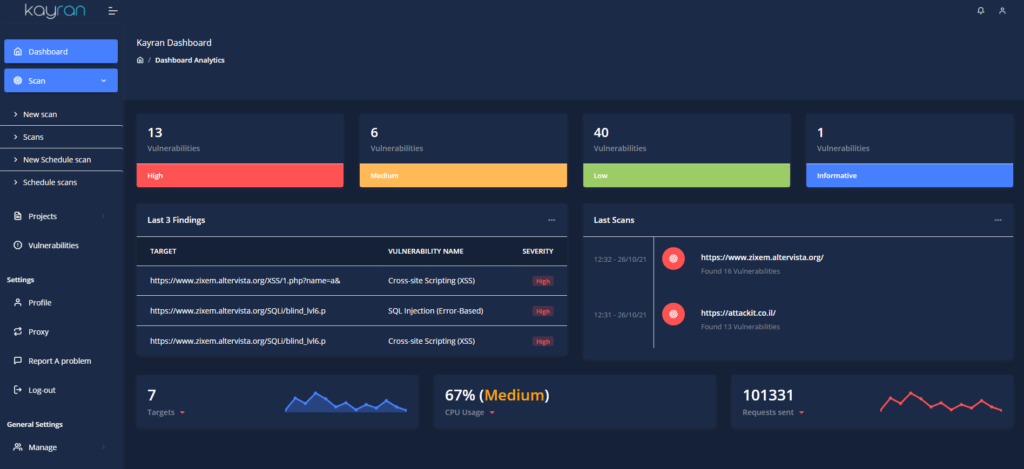
What truly makes us unique is the power that you have been given your hands. CYTRIX allows you to map your weakest points in your web assets, align them by their severity and adjust the fixing to the most urgent vulnerabilities.
More than that, CYTRIX aims to achieve only legitimate exploitable vulnerabilities using the “Monitoring” System, so you won’t waste your time.
We hold more than 15,000 CVE’s, Over 9000 vulnerabilities and etc..
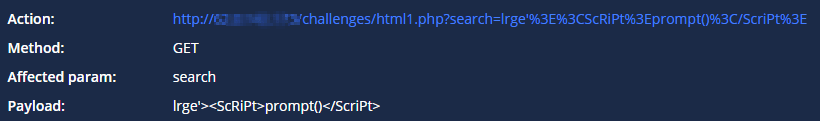
CYTRIX presents an accurate payload of exploit that was used during our scans, which also includes clear instructions that will allow you to perform the same exploitation by yourselves in order to learn about it better.
We are proud to say that our web scanner is the only tool that has the option of scanning SPA websites!
We use new methods combined with a powerful automation process to reduce server resources and complete the scan at extremely high speeds.
Three years ago, we would do everything manually, Penetration Testing/investigations, and extract information.
To do several things at the same time we needed more manpower and also pay money to a lot of different companies for a number of different tools.
So Sahar Avitan & Eden Zaraf started working on “CYTRIX”.
Today the tool is able to scan quickly, efficiently, prevent a large number of False positives from other competitors, to exploit vulnerabilities at the highest level.
and most importantly? User-friendly, and goes over every piece of information that exists in assets.
In short, join us.
If you’re in the main site (https://cytrix.io/), click on “LOGIN” located in the main navigation bar.
‘Targets’ are URLs that you wish to Scan.
For example: https://mywebsite.com is a Target.
Kayran allows you to stay protected from unknown security vulnerabilities that could be “hiding” in your online assets.
Besides that, Kayran will generate a full report displaying the vulnerabilities found and how to fix them, so you can patch, upgrade and stay protected while continue doing your best work.
Kayran is able to scan and find vulnerabilities in sites that no tool can find, such as SPA sites, in addition, Kayran exploits any ZERO DAY vulnerability that exists – and most importantly the high-speed relative to the market.
No! Kayran is a tool that runs on your browser, just make sure your browser is supported and updated.
In fact, Kayran was designed to be user-friendly and easy to use even for people without technical knowledge. Introduction to Kayran’s Dashboard
Sure you can! just schedule a meeting through here, we’ll have a “Demo” meeting, showing and explaining everything about Kayran.
Kayran does not give any third-party direct or indirect access to the customer’s data except at your directive or when it’s required by law.
You can use our Support.
EULA stands for end-user license agreement. A EULA specifies in detail the rights and restrictions which apply to the use of the software. Reading and Agreeing to it means that you agree to everything written in it and that you are legally required to do so.
Kayran has a dedicated system that knows how to keep your assets secure, the systems will not fall at any stage, and the exploitation of the vulnerabilities will not harm the information or the site.
Kayran will display the targets got scanned, vulnerabilities it detected, requests and so on – only to the user/client using the server.
Every browser.
If you encounter any compatibility issues, please contact us.
No, Kayran has a special “Speed” engine which will detect when a overload is potential, and preventing it by dynamically changing the number of requests it will send.
Of course! just contact us via your given contact mail or leave a message.
There are two ways to do that:
Using the New Scan under Scan so that we can define everything we want to be used in the scan in a more detailed way.
Yes! simply create a new Project (Projects → New Project) and then, when initiating the scan, select your desired Project (Settings → Project).
Yes! by using our API Documentation !
Problem? no problem! simply tell us through the “Report A Problem” section found in Kayran’s main menu, or, mail us at [email protected]
Yes! and currently, Kayran is the only tool that can do it!
Of course! by using a Proxy.
No! After initiating a Scan, as long as your Server is active, it will continue without requiring you to stay logged in. You can even turn off your device!
The vulnerabilities that Kayran has detected will be categorized according to their level of severity and the level of potential damage they may cause, when the lowest severity is Informative and the highest, is High.
If you initiate a new scan with multiple targets, they will be moved to the active scans section according to the plan you’ve purchased (if none of them will be moved, you’ve either ran out of domains or exceeded the number of active scans you’re allowed).
Mark the vulnerability as FalsePositive and we will check it out as soon as possible!
Simple! you can create and use our highly advanced “Self Login” method.
Yes, simply create a new Proxy using it.
Yes! learn more about it below :
You can either use your own by creating a proxy Creating and Setting up Proxy Profiles
Or, you can get one from us Requesting a Fixed IP
Yes, and you can also define certain roles for each of them.
There’s NO LIMIT on the number of Users you can add to your Server.
To change your personal details, use the Profile section.
There are 4 Types of Roles for users in Kayran. Each with its own Privileges and Capabilities.
To learn more – Roles Explained
Yes, for more information, read our Reports section in Support
Yes, you can attach scans to projects in each stage it goes through (even after being completed).
Yes, you can set it up in your Profile. Just toggle “On Change Status Scan” on.
Setting up Email Notifications
Yes, you can set it up in your Profile. Just toggle “On Stop” on.
Yes, you can set it up in your Profile.
Yes, you can set it up in your Profile.
Yes, simply navigate to the “Server Settings” and, change it there.
For more information, read here :
We have a number of Integration which users can use in Kayran such as Shodan and Microsoft Teams.
The Integration Support section is being updated as they are.
There are many Modifiers you can set. From the Description to the Proxy being used.
To learn more about Modifiers.
Currently, you can change the Description, Project, Speed and Level Deep (if defined manually) and Jira Project.
Use our Support to learn more.
Yes. By uploading your API’s Schema, Kayran can Scan and Detect Vulnerabilities in it.
Each Release, Kayran’s clients gets an Email listing all changes. You can also view them here.
Yes, you can do it Manually, or, you can use the Duplicate function located in the table in Scans.
Enumeration is the act of “Brute Forcing”, overloading the server by “Inserting” random Parameters and Paths used for testing.
Use it in the Crawler tab when initiating new scans.
Pay attention that enabling Enumeration Significantly extends the Scan’s Duration.