What is a VPN? Why should someone be using VPN? Which Problems does is solve? and what is the advantages and disadvantages of it? Let’s dive in.
A VPN or a Virtual Private Network is a service meant for transferring private information over an infrastructure. That infrastructure is mainly or entirely publicly owned or privately owned with access to the general public.

The Problems a VPN solves
Remote networks can be connected via the Internet. But this connection creates two main problems :
- The remote network resources are not available and this is because it is not possible to contact remote private addresses because they are not unique. For example: if the address of the remote server is 192.168.1.100/24, then it is not possible to contact it via the Internet because it is a private address and not unique like a public addresses.
- There is a danger to the confidentiality of the information. The information that passes through the Internet is exposed to citation (Sniffing) and this is because the Internet is a public place.
And they are solved by
- A VPN connects a computer (Remote Access VPN) or a branch (Site-to-Site IPsec VPN) to a remote network, as if they were connected to the same LAN network. Therefore, once the VPN connection is active, remote private addresses can be accessed.
- VPN encrypts the information and thus creates a secure connection. Therefore, only the users involved in the VPN connection can decipher the information being transferred.
The Advantages of using VPN:
- Connectivity between Private Networks – it knows how to connect private addresses via the Internet.
- Security – The information transmitted via VPN is secured by Internet Protocol Security (aka IPsec) and Secure Sockets Layer ( aka SSL).
- Financial savings – the use of VPN prevents the high cost of leased lines (WAN). Therefore, VPN is a more economical way to connect branches.
- Expansion – you can easily and quickly connect additional remote branches and users. Many companies see this as an advantage because the ambition of every company is to grow and develop.
There are certain, specific goals we can achieve using a Virtual Private Network:
- Accessing – All the content on Netflix is not available in your country for some reason? use a VPN! (Not that we encourage this in any way). By using it, you can access Content and Domains that are blocked to you by your ISP.
- “Disguise” – Want to download or watch your favorite animes online but are afraid of being recognized? Simple! By using a Virtual Private Network of any kind, you are now actually someone else! People use it order to purchase things online by impersonating users from other countries to get cheaper prices than in their own country. Often, this feature is misused to perform unethical activities.
The Types
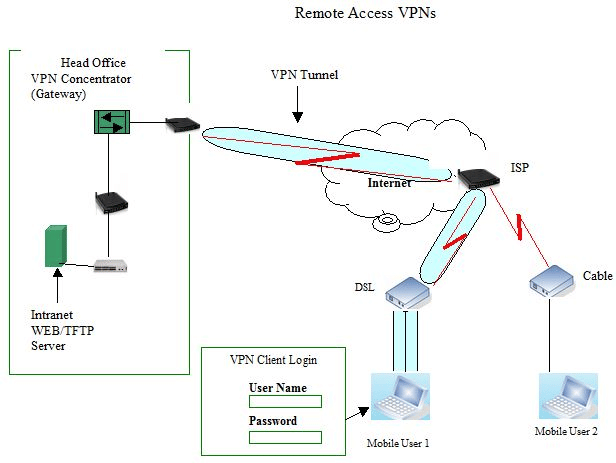
Remote Access
Like its name, Remote Access VPN allows a remote client to log into the organization and securely access resources and information belonging to the organization. There are two ways to to this:
- The User/Client uses a browser to enact the VPN. Off course the connection is secured using HTTPS.
- The User/Client uses a software that was adapted for his use and installed on his computer. Through this software, it’s possible to connect to the VPN server.
Site-to-Site IPSec (Internet Protocol Security) VPN
This time, this type focuses on creating a direct and secure connection between two branches. IP security (IPsec) is typically used to create and secure a Site-to-Site VPN.
Dynamic Multipoint VPN (DMVPN)
The previous types of VPN are not effective for situations where there are more than a number of sites. The reason for this is that each site will require static configurations for all other sites.
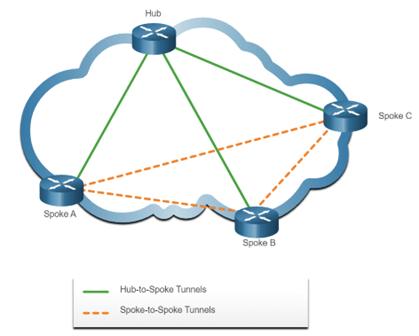
DMVPN provides us with the capability of creating a dynamic-mesh Virtual Private Network without having to pre-configure (static) all possible tunnel end-point peers. Thus, solving the issue mentioned above.
In conclusion, if you are here, you have already understood that the Internet and in general, all types of networks are things that we should not take lightly when used. And we will also understand that any tool that helps us prevent any attack of any kind on our information is welcomed. That’s why using this type of network, and in general, the use of the term and its name are so familiar to you.
One tool that might assist you in protecting yourself and your information, is Cytrix, for example.
Cytrix is a Web Application Vulnerability Scanner that detects all sorts of Vulnerabilities that may leaving you exposed to attacks against your Web Assets. That includes the fact that Cytrix can search for Vulnerabilities in different types of VPNs!
Stay safe, choose Cytrix.