Throughout our lives we have learned that almost everything has a value.
Whether it’s your car, phone and even a piece of paper lying down on the floor in your house, everything you own is an Asset.

From the image above, we understand that, because your assets have value, they also have a price.
Let’s talk about Assets
Firstly, it’s important to understand that there are two types of assets :
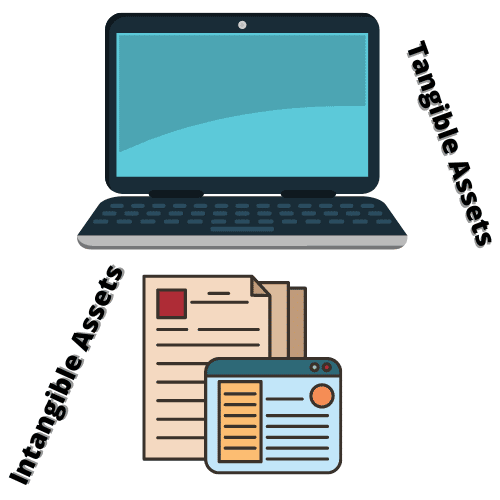
- Tangible Assets – these types of assets are physical, things you can “touch” and see clearly.
For example : Computers, Cars, a House, and even clothes, such assets usually have a price / value that does not change, and sometimes even loses its value over time.
2. Intangible Assets – these types of assets (usually) can’t be “touched”, they don’t exist physically.
When talking about Intangible Assets, we usually refer to data / information that has a certain value.
For example : Algorithms, Ideas, Personal Information and Passwords.
These Assets can have a value of thousands, and even millions of dollars, if the secrets of a company worth millions will spread, that could immediately lead to it’s collapse!
Also, the value of these types of Assets usually increases over the years (if they make money of course), just try to imagine the value behind the idea behind “Facebook” in 2004 compared to its value today!
Resources and Risks Management
So we understood what types of Assets exist, how do we know which is more important to us?
It is important to know how to differ them from one to another and to understand one very important thing : On which Asset we will invest more resources in order to protect it
There are a number of steps required to accomplish this task :
- Identifying – first of all, it is important to identify and understand what the assets of the organization are. Is it related to the company? What kind of asset is it?
- Assessment – evaluate the value of each asset in the organization.
Does it worth the investment of resources in it? How much this asset is worth to the organization? (in terms of capital). - Risk Assessment – and finally, it’s important to understand the risks.
Is the asset really at risk? What types of risks will we face? (Exposure, Theft and so on).
After all these steps, we will know how to allocate our resources appropriately and in an orderly manner so that we can secure each asset according to it’s calculated value.
So don’t forget to “calculate” yourself better !
Stay safe, choose Cytrix.