Like mentioned here, There are several HTTP request methods, each with its own purpose and uses,
In this article we’ll talk about the TRACE Method.
The TRACE (also known as TRACK) method main purpose is diagnostics, being used to perform a message loop-back test that tests the path for the target resource.
We also use the TRACE and TRACK methods to debug web server connections.
When enabled, the TRACE method, similar to the name of the method, will be used by requests being sent, then, in response, the Web Server will “Echo” and return their “Reflection” in his response the same way.
The final recipient of the request should reflect the message received, leaving out some of the fields, back to the client.

As you can see in the picture above, each Method works differently, each with its own advantages and disadvantages.
When using the TRACE method :
- The request has no Body.
- It cannot be cached.
- It’s considered “Safe” (below we will talk about the risks involved).
- It’s not allowed in HTML forms.
- Doesn’t have any side effects (besides keeping statistics).
Generally, using TRACE has no serious consequences, but, we know there are no perfect things in this world,
Let’s talk about the risks that need to be taken into account when talking about the TRACE method.
Occasionally, this may lead to sensitive information being displayed to a local or remote unprivileged user, that, abuses the way that the TRACE/TRACK function to gain access to sensitive information in HTTP headers when making HTTP requests, to steal legitimate users’ credentials, allowing him to initiate Cross Site Tracing attacks (known as XST).
Note that new, modern browsers no longer allow the use TRACK and TRACE methods from JavaScript to prevent such types of attacks.
Still, the TRACK and TRACE methods might still be of use to an attacker in cases where the request passes through intermediary (middle) systems which add headers or other, sensitive information to the request before forwarding it onto the server, building the response, meaning that the information that was added is now exposed to a potential attacker.
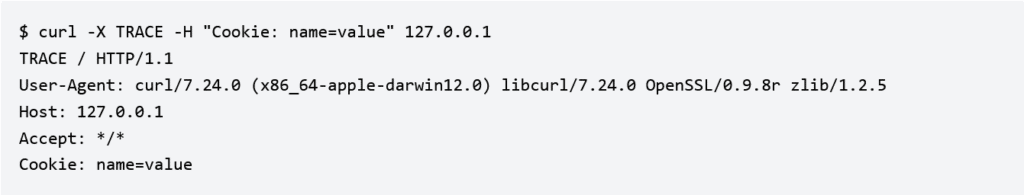
That’s scary, isn’t it?
Our recommendation is to (if using Apache versions 1.3.34, 2.0.55 and later) set the TraceEnable directive to “off” in the main configuration file and then restart Apache.
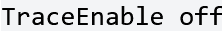
Stay safe, and “TRACE” on my friends,
Choose Cytrix.