As we know, a conversation need at least 2 people to exist, in this conversation of course, the exchange of data and information are being made, but, is the conversation and the information exchanged in it secure and available only to the people participating in it? for that, we use the Fine Art of Cryptography.
When talking about DATA (or Information), it can exist in these forms :
- Information in “Motion” – for example, Information flowing online like chat messaging and so on.
- “Resting” Information (static) – like passwords and user credentials stored on the server.
- Information in use – Information stored and used in the RAM memory is a good example.
We can understand that, since the data exists in a number of forms, there are several ways to obtain them.
So, no matter what, it’s important to use Cryptography in order to Encrypt and “hide” this DATA.
It seems that through the use of Cryptography, the CIA Model (also know as Triad) is being carried out :
- Confidentiality – implemented by encryption.
- Integrity – implemented by Hashing.
- Authentication – by ensuring that the information did indeed come from the source.
The main thing guaranteed as a result of using Cryptography is that even if the information “leaks” out, only people who knew how this specific encryption works will be able to understand the message.
Here are some examples of Cryptography :
Caesar Cipher
This encryption method is quiet simple, you decipher it by taking the letters found in the encrypted message and simply replacing them with a certain letter that comes after, or, before it, based on the decryption key.
For example : if the encrypted message is “ABC” and the decryption key is +1 the answer is –
“A” = “B”, “B” = “C” and “C” = “D”, so the decipherment of this message is “BCD”.


Can you guess what’s written here “Lbzsbo jt uif cftu!” ? (the decryption key is – 1).
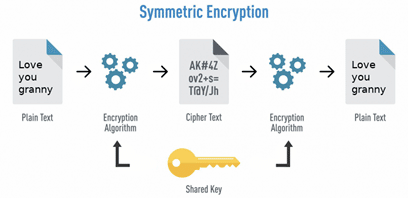
Symmetric Encryption (shared-key encryption)
It’s a two-way mathematical algorithm that uses a single key to encrypt / decrypt information.
Both sides use the same key (also known as Session key).
Usually, the algorithm is known to all and confidentiality is maintained as long as the key is being kept that way.
Pros :
- Encryption is very fast.
- Encryption does not require high processing power.
Disadvantages :
- Using a single key that encrypts as well as decrypts, requires the key to be sent to the recipient of the encrypted information. Therefore the key is prone to theft.
- Encrypting a lot of information with the same key makes it possible to discover the key.
Asymmetric Encryption (public-key encryption)
It is a two-way mathematical algorithm that uses two keys to encrypt / decrypt information.
- Public-key – Used for encryption and distributed freely to anyone we want to send us encrypted information (for example, a Username).
- Private-key – Used to decrypt.
Information encrypted using the public key is decrypted only by means of the private key (for example, a password).
Stay encrypted, choose Cytrix.