Besides the most creative title you’ve ever seen, there are many things we do not like that we can talk about, in this case, we will talk about a certain type of attacks called: “Injection Attacks” (insert loud TAM TAM TAMMM noise).
No one likes to get a shot, me personally was afraid of syringes until the age of 16!
And for a good reason, it’s not just the needle that scares me, but the fact that we insert a certain “material” that did not exist before that, it can cause harm, side-effects, and even trigger new allergies.

Just like that, Injection attacks works in a similar way:
It wasn’t “inside” before, you’ll probably won’t like it, and it will cause certain changes to occur.
All Injection Attacks works in the same way, through a certain input the attacker writes, the platform\system will process it “thinking” it’s a valid input but instead can lead to many, unwanted results.
There are a number of Injection attacks types :
- XSS Attacks (Cross-Site-Scripting) – probably the worst of them all, relevant to websites and Web-Apps, the attacker injects a code (particularly in JavaScript) and by performing it, he can “Break Tags” or simply overriding what the form is actually supposed to do, for example, this lovely website –
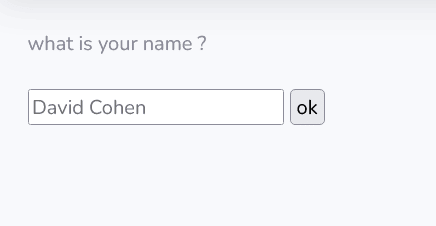
expect an Key-Input which is the Full name of a certain person, But, what if instead we will insert a certain code in HTML? we can “break open” the Tag or the Command responsible for the input box that will now be gone, replaced, or even recording for us all the input from now on.
We have couple of XSS types –
- Persistent\Stored – when the attacker managed to inject the code so it stays in a certain database and “comes back” (yes, Terminator reference) every time a user loads the page and infects him.
- Reflected – after the “victim” sends a request, the the server responds and then infects the victim.
- DOM based – when the attacker sends the malicious string of code through the URL bar, then the code “Enters” the page and perform a certain action, the vulnerability is on the User-Side code and not on the server.
- SQL Injection – Is a particularly widespread and dangerous form of injection, in this case, the attacker needs to finds a certain interaction between the Web-App to some sort of database,which implies for SQL-relation, insert a Malicious-”DR. EVIL”-commands and BAM!, well, you know the rest…
You must be very scared after reading all this, and getting a vaccine injection sounds good in comparison,
REMEMBER – don’t forget to embed an algorithm or code responsible for Input Validation in your system, which is preventing in the first place Untrusted strings, and avoid Accessing External Interpreters preventing the attacker from using, for example, Shell commands and so on.
Afraid of needles?
Remember that you can always trust the PROS,
With clean needles and the best doctors around, we will help you to better defend yourself against all sorts of threats.
Stay safe, choose Cytrix.